This service converts a FLV file (Youtube's movie,etc) to another format (AVI/MOV/MP4/MP3/3GP). The service is using a unique technologies (JP), and converts FLV to MPEG4 faster and losslessy than a typical transcoder.
When you submit an url, this service will download and convert the video format. Then you can download the converted file.
http://vixy.net/flv_converter
segunda-feira, dezembro 18, 2006
domingo, novembro 26, 2006
sábado, novembro 25, 2006
20 Must Read HOWTOs and Guides for Linux
http://www.foogazi.com/2006/11/24/20-must-read-howtos-and-guides-for-linux
sexta-feira, novembro 24, 2006
Security Configuration Guides
NSA initiatives in enhancing software security cover both proprietary and open source software, and we have successfully used both proprietary and open source models in our research activities. NSA's work to enhance the security of software is motivated by one simple consideration: use our resources as efficiently as possible to give NSA's customers the best possible security options in the most widely employed products. The objective of the NSA research program is to develop technologic advances that can be shared with the software development community through a variety of transfer mechanisms. NSA does not favor or promote any specific software product or business model. Rather, NSA is promoting enhanced security.
http://www.nsa.gov/snac/index.cfm?MenuID=scg10.3.1
http://www.nsa.gov/snac/index.cfm?MenuID=scg10.3.1
domingo, novembro 05, 2006
Linux Kernel Swear Counts
http://www.vidarholen.net/contents/wordcount
http://durak.org/sean/pubs/kfc
http://durak.org/sean/pubs/kfc
sábado, novembro 04, 2006
No More Ads in your Firefox!
Get this plugins:
Adblock:
https://addons.mozilla.org/firefox/1865
FlashBlock:
https://addons.mozilla.org/firefox/433
Adblock:
https://addons.mozilla.org/firefox/1865
FlashBlock:
https://addons.mozilla.org/firefox/433
segunda-feira, outubro 30, 2006
Arudius
Arudius is an information assurance (IA) Linux live CD with tools for penetration testing and vulnerability analysis. IA has many other aspects besides network security. However, it seems that the mainstream public identifies informaion assurance primarily with securing network-enabled systems, so we decided to go with the mainstream and call Arudius a tool for information assurance. The CD consists of a Zenwalk Linux base on top of which a large collection of network security testing software (full list) has been installed - including tools listed on Insecure.org Top 75 list plus many other tools listed on Freshmeat, Sf.net and other information assurance sites around the world.
http://arudius.sourceforge.net
http://arudius.sourceforge.net
segunda-feira, outubro 23, 2006
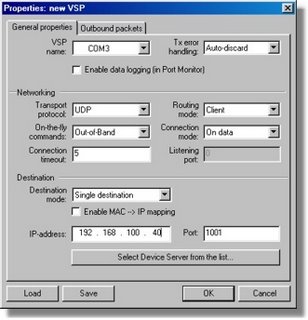
Virtual Serial Port Driver
A virtual serial port is a trade term used by certain vendors of COM port redirector software that emulates a serial port (RS-232, RS-422, and RS-485). This port is created by special software products which enable extra serial ports in operation system without additional hardware installation (such as expansion cards, etc.). Unlike the standard physical serial port the virtual one can be assigned any name (COM255, VSP33, etc.) to. It is possible to create unlimited number of virtual serial ports in your PC. The only limitation is the performance capacity of your system, as it may require a substantial amount of resources to emulate say 255 serial ports on slow computers.
Virtual serial port emulates all serial port functionality, including Baud rate, Data bits, Parity bits, Stop bits, etc. Additionally it allows controlling the data flow, emulating all signal lines (DTR/DSR/CTS/RTS/DCD/RI) and customizing pinout (only advanced solutions).
Serial ports emulation can be useful in case there is a lack of available physical serial ports or they do not meet the current requirements. For instance, virtual serial ports can help you share data between several applications from one GPS device connected to serial port. Another option is to communicate with any other serial devices via internet or LAN as if they are locally connected to computer (Serial-over-Ethernet technology). You can establish connection between two computers or applications via emulated null-modem link. Most of the available virtual serial port emulators are compatible with Windows 9x, Windows NT, Windows 2000, Windows ME, Windows 2003, Windows XP and some of them run under Windows CE, Windows Mobile and Pocket PC.
Virtual serial ports are available as both commercial products and free software.
Virtual Serial Port Driver (VSPD) turns serial ports of Tibbo Device Servers into remote COM ports of your PC. VSP Manager is used to create and manage Virtual Serial Ports (VSPs).
http://www.tibbo.com/vspdl.php
Virtual serial port emulates all serial port functionality, including Baud rate, Data bits, Parity bits, Stop bits, etc. Additionally it allows controlling the data flow, emulating all signal lines (DTR/DSR/CTS/RTS/DCD/RI) and customizing pinout (only advanced solutions).
Serial ports emulation can be useful in case there is a lack of available physical serial ports or they do not meet the current requirements. For instance, virtual serial ports can help you share data between several applications from one GPS device connected to serial port. Another option is to communicate with any other serial devices via internet or LAN as if they are locally connected to computer (Serial-over-Ethernet technology). You can establish connection between two computers or applications via emulated null-modem link. Most of the available virtual serial port emulators are compatible with Windows 9x, Windows NT, Windows 2000, Windows ME, Windows 2003, Windows XP and some of them run under Windows CE, Windows Mobile and Pocket PC.
Virtual serial ports are available as both commercial products and free software.
Virtual Serial Port Driver (VSPD) turns serial ports of Tibbo Device Servers into remote COM ports of your PC. VSP Manager is used to create and manage Virtual Serial Ports (VSPs).

http://www.tibbo.com/vspdl.php
w3bfukk0r - scan webservers for hidden directories (forced browsing)
w3bfukk0r is a forced browsing tool, it basically scans webservers (HTTP/HTTPS) for a directory by using HTTP HEAD command and brute force mechanism based on a word list. Features:
* HTTP/HTTPS(SSL) support
* Banner grabbing
* User-Agent faking
* Proxy support (HTTP/S)
* Reports found and non-existend directories
http://www.ngolde.de/w3bfukk0r.html
* HTTP/HTTPS(SSL) support
* Banner grabbing
* User-Agent faking
* Proxy support (HTTP/S)
* Reports found and non-existend directories
http://www.ngolde.de/w3bfukk0r.html
Medusa Parallel Network Login Auditor
Medusa is intended to be a speedy, massively parallel, modular, login brute-forcer. The goal is to support as many services which allow remote authentication as possible. The author considers following items as some of the key features of this application:
* Thread-based parallel testing. Brute-force testing can be performed against multiple hosts, users or passwords concurrently.
* Flexible user input. Target information (host/user/password) can be specified in a variety of ways. For example, each item can be either a single entry or a file containing multiple entries. Additionally, a combination file format allows the user to refine their target listing.
* Modular design. Each service module exists as an independent .mod file. This means that no modifications are necessary to the core application in order to extend the supported list of services for brute-forcing.
http://www.foofus.net/jmk/medusa/medusa.html
* Thread-based parallel testing. Brute-force testing can be performed against multiple hosts, users or passwords concurrently.
* Flexible user input. Target information (host/user/password) can be specified in a variety of ways. For example, each item can be either a single entry or a file containing multiple entries. Additionally, a combination file format allows the user to refine their target listing.
* Modular design. Each service module exists as an independent .mod file. This means that no modifications are necessary to the core application in order to extend the supported list of services for brute-forcing.
http://www.foofus.net/jmk/medusa/medusa.html
sábado, outubro 07, 2006
Beryl
Beryl is a combined window manager and compositing manager that runs on top of Xgl or AIGLX using OpenGL to provide effects accelerated by a 3D graphics card on the desktop.
What is the difference between freedesktop.org compiz and beryl?
* Uses flat file backend instead of gconf meaning almost no gnome dependency.
* Needs "beryl-settings", an application to configure settings instead of gconf-editor.
* Has a lot of extra plugins and enhanced features in other plugins.
* Starts with beryl-manager.
* Has a themeable decorator (emerald).
* Has a theme manager (emerald-themer).
* Changes frequently: new features are added on a daily basis.
* Made by a community right here at forum.beryl-project.org, although submissions of extra plugins and enhancements from here to freedesktop would make the compiz better over all.
http://wiki.beryl-project.org/index.php/Main_Page
http://forum.beryl-project.org/
What is the difference between freedesktop.org compiz and beryl?
* Uses flat file backend instead of gconf meaning almost no gnome dependency.
* Needs "beryl-settings", an application to configure settings instead of gconf-editor.
* Has a lot of extra plugins and enhanced features in other plugins.
* Starts with beryl-manager.
* Has a themeable decorator (emerald).
* Has a theme manager (emerald-themer).
* Changes frequently: new features are added on a daily basis.
* Made by a community right here at forum.beryl-project.org, although submissions of extra plugins and enhancements from here to freedesktop would make the compiz better over all.
http://wiki.beryl-project.org/index.php/Main_Page
http://forum.beryl-project.org/
segunda-feira, outubro 02, 2006
domingo, outubro 01, 2006
segunda-feira, setembro 11, 2006
Spamer was condemned in Virginia
The Court of Appeals of Virginia upheld yesterday what is believed to be the first conviction in the nation under a state anti-spamming law that makes it a felony to send unsolicited mass e-mails.
A North Carolina man was convicted in Loudoun County two years ago of illegally sending tens of thousands of e-mails to America Online customers. Prosecutors said Jeremy Jaynes flooded the servers at the Internet company's headquarters in Loudoun with bulk e-mail advertisements for computer programs and stock pickers.
Jaynes was sentenced last year to nine years in prison on three counts of violating the state's anti-spam law and was allowed to remain free on $1 million bond while his case was appealed. Thomas M. Wolf, an attorney for Jaynes, said he plans to appeal yesterday's decision.
source: http://www.washingtonpost.com/wp-dyn/content/article/2006/09/05/AR2006090501166.html
and http://it.slashdot.org/article.pl?sid=06/09/08/1237230
A North Carolina man was convicted in Loudoun County two years ago of illegally sending tens of thousands of e-mails to America Online customers. Prosecutors said Jeremy Jaynes flooded the servers at the Internet company's headquarters in Loudoun with bulk e-mail advertisements for computer programs and stock pickers.
Jaynes was sentenced last year to nine years in prison on three counts of violating the state's anti-spam law and was allowed to remain free on $1 million bond while his case was appealed. Thomas M. Wolf, an attorney for Jaynes, said he plans to appeal yesterday's decision.
source: http://www.washingtonpost.com/wp-dyn/content/article/2006/09/05/AR2006090501166.html
and http://it.slashdot.org/article.pl?sid=06/09/08/1237230
domingo, setembro 10, 2006
Splitting Large Files to Span Multiple Disks using TAR
The two extra command line options you need to use over and above the standard syntax are -M (--multi-volume) which tells Tar you want to split the file over multiple media disks. You then need to tell Tar how big that media is, so that it can create files of the correct size. To do this you use the --tape-length option, where the value you pass is number x 1024 bytes.
The example below shows the syntax used. Lets say the largefile.tgz is 150 Meg and we need to fit the file on two 100 Meg Zip drives.
tar -c -M --tape-length=102400 --file=disk1.tar largefile.tgz
The value 102400 is 1024 x 100, which will create a 100 Meg file called disk1.tar and then Tar will prompt for volume 2 like below :-
Prepare volume #2 for disk1.tar and hit return:
In the time of tape drives you would have taken the first tape out of the machine and inserted a new tape, and pressed returned to continue. As we want Tar to create the remaining 50 Meg in a separate file, we issue the following command :-
n disk2.tar
This instructs Tar to continue writing the remaining 50 Meg of largefile.tgz to a file named disk2.tar. You will then be prompted with the line below, and you can now hit return to continue.
Prepare volume #2 for disk2.tar and hit return:
You would repeat this process until your large file has been completely processed, increasing the disk number in the file each time you are prompted.
Other example:
tar cvf arq1.tar -M --tape-length=500000 bigarq.txt
Putting the File Back Together
The process is similar when putting the large file back together from its split-up files. Below is the syntax used to re-create the large file from the disk1.tar and disk2.tar images.
C:\tar>tar -x -M --file=disk1.tar largefile.tgz
Prepare volume #2 for disk1.tar and hit return: n disk2.tar
Prepare volume #2 for disk2.tar and hit return:
Source: http://www.cgi-interactive-uk.com/splitting_large_files.html
The example below shows the syntax used. Lets say the largefile.tgz is 150 Meg and we need to fit the file on two 100 Meg Zip drives.
tar -c -M --tape-length=102400 --file=disk1.tar largefile.tgz
The value 102400 is 1024 x 100, which will create a 100 Meg file called disk1.tar and then Tar will prompt for volume 2 like below :-
Prepare volume #2 for disk1.tar and hit return:
In the time of tape drives you would have taken the first tape out of the machine and inserted a new tape, and pressed returned to continue. As we want Tar to create the remaining 50 Meg in a separate file, we issue the following command :-
n disk2.tar
This instructs Tar to continue writing the remaining 50 Meg of largefile.tgz to a file named disk2.tar. You will then be prompted with the line below, and you can now hit return to continue.
Prepare volume #2 for disk2.tar and hit return:
You would repeat this process until your large file has been completely processed, increasing the disk number in the file each time you are prompted.
Other example:
tar cvf arq1.tar -M --tape-length=500000 bigarq.txt
Putting the File Back Together
The process is similar when putting the large file back together from its split-up files. Below is the syntax used to re-create the large file from the disk1.tar and disk2.tar images.
C:\tar>tar -x -M --file=disk1.tar largefile.tgz
Prepare volume #2 for disk1.tar and hit return: n disk2.tar
Prepare volume #2 for disk2.tar and hit return:
Source: http://www.cgi-interactive-uk.com/splitting_large_files.html
sexta-feira, setembro 08, 2006
SMTP reply codes
500 Syntax error, command unrecognized [This may include errors such as command line too long]
501 Syntax error in parameters or arguments
502 Command not implemented
503 Bad sequence of commands
504 Command parameter not implemented
211 System status, or system help reply
214 Help message [Information on how to use the receiver or the meaning of a particular on-standard command; this reply is useful only to the human user]
220 Service ready
221 Service closing transmission channel
421 Service not available, closing transmission channel [This may be a reply to any command if the service knows it must shut down]
250 Requested mail action okay, completed
251 User not local; will forward to
450 Requested mail action not taken: mailbox unavailable [E.g., mailbox busy]
550 Requested action not taken: mailbox unavailable [E.g., mailbox not found, no access]
451 Requested action aborted: error in processing
551 User not local; please try
452 Requested action not taken: insufficient system storage
552 Requested mail action aborted: exceeded storage allocation
553 Requested action not taken: mailbox name not allowed [E.g., mailbox syntax incorrect]
354 Start mail input; end with.
554 Transaction failed
Source: RFC 821
501 Syntax error in parameters or arguments
502 Command not implemented
503 Bad sequence of commands
504 Command parameter not implemented
211 System status, or system help reply
214 Help message [Information on how to use the receiver or the meaning of a particular on-standard command; this reply is useful only to the human user]
220
221
421
250 Requested mail action okay, completed
251 User not local; will forward to
450 Requested mail action not taken: mailbox unavailable [E.g., mailbox busy]
550 Requested action not taken: mailbox unavailable [E.g., mailbox not found, no access]
451 Requested action aborted: error in processing
551 User not local; please try
452 Requested action not taken: insufficient system storage
552 Requested mail action aborted: exceeded storage allocation
553 Requested action not taken: mailbox name not allowed [E.g., mailbox syntax incorrect]
354 Start mail input; end with
554 Transaction failed
Source: RFC 821
quarta-feira, setembro 06, 2006
Convert CUE/BIN images to ISO in Linux
It's simple:
bchunk image.bin image.cue image.iso
Then you can mount ISO image with "mount" command:
mount -o loop -t iso9660 image.iso /mnt
bchunk image.bin image.cue image.iso
Then you can mount ISO image with "mount" command:
mount -o loop -t iso9660 image.iso /mnt
terça-feira, agosto 22, 2006
Linux Test Tools
The purpose of this Linux Test Tools Table is to provide the open-source community with a comprehensive list of tools commonly used for testing the various components of Linux.
http://ltp.sourceforge.net/tooltable.php
http://ltp.sourceforge.net/tooltable.php
domingo, agosto 06, 2006
sábado, agosto 05, 2006
Comparison of Linux distributions
The many available Linux distributions differ for a range of reasons including technical, organizational, and philosophical.
Technical variations include support for different hardware devices and systems or software package configurations. Organizational differences may be motivated by technical decisions but also by philosophical or even historical reasons. Some distributions specialise in use on desktops, servers or routers. Other criteria include security, including how quickly security upgrades are available; ease of package management; and number of binary packages available.
These tables compare the latest stable release of major distributions on a range of objective criteria. It does not cover the subjective merits of each operating system, branches marked as unstable/beta, nor compare Linux distributions with other operating systems.
Look at: http://en.wikipedia.org/wiki/Comparison_of_Linux_distributions
Technical variations include support for different hardware devices and systems or software package configurations. Organizational differences may be motivated by technical decisions but also by philosophical or even historical reasons. Some distributions specialise in use on desktops, servers or routers. Other criteria include security, including how quickly security upgrades are available; ease of package management; and number of binary packages available.
These tables compare the latest stable release of major distributions on a range of objective criteria. It does not cover the subjective merits of each operating system, branches marked as unstable/beta, nor compare Linux distributions with other operating systems.
Look at: http://en.wikipedia.org/wiki/Comparison_of_Linux_distributions
sexta-feira, agosto 04, 2006
Warsaw's Laws of Hackering
In the great tradition of Murphy's Law and other related laws, I offer my humble few. I'm not sure I have rightful claim to originating all these, so if you find a previous reference to these laws, please let me know!
Warsaw's First Law: The Rule of Estimate Accuracy Insurance
When making a time estimate for any programming task, make your best formalized guess, then multiply by two and bump it up a unit. E.g. "I think it will take me three days to hack in those changes to the frobnicator"; My official estimate: 6 weeks.
Warsaw's Second Law: Unbending Law of Commit Scheduling
Never change anything after 3pm on a Friday.
Corollary to Warsaw's Second Law
If you do change anything after 3pm on Friday, you will break it, and thus end up fixing it for the entire weekend. You will probably not be able to sleep, and if you do fall asleep, you will dream about the breakage. On Monday morning, you will fix the problem in five minutes.
Warsaw's Third Law: Law of Software in a Vacuum
All software sucks. Make sure yours sucks less.
Warsaw's Fourth Law: The Law of Pinball Machine Instructions
It doesn't matter a wit if the instructions are printed clearly for all to see, nobody will read them. They'll just drop their quarters and start pushing buttons like a Tommy. Software is the same.
Warsaw's Fifth Law: A Rose By Any Other Name (a.k.a the Pink Floyd Rule)
All names are stupid until you become rich and famous with it.
Source: http://barry.warsaw.us/software/laws.html
Warsaw's First Law: The Rule of Estimate Accuracy Insurance
When making a time estimate for any programming task, make your best formalized guess, then multiply by two and bump it up a unit. E.g. "I think it will take me three days to hack in those changes to the frobnicator"; My official estimate: 6 weeks.
Warsaw's Second Law: Unbending Law of Commit Scheduling
Never change anything after 3pm on a Friday.
Corollary to Warsaw's Second Law
If you do change anything after 3pm on Friday, you will break it, and thus end up fixing it for the entire weekend. You will probably not be able to sleep, and if you do fall asleep, you will dream about the breakage. On Monday morning, you will fix the problem in five minutes.
Warsaw's Third Law: Law of Software in a Vacuum
All software sucks. Make sure yours sucks less.
Warsaw's Fourth Law: The Law of Pinball Machine Instructions
It doesn't matter a wit if the instructions are printed clearly for all to see, nobody will read them. They'll just drop their quarters and start pushing buttons like a Tommy. Software is the same.
Warsaw's Fifth Law: A Rose By Any Other Name (a.k.a the Pink Floyd Rule)
All names are stupid until you become rich and famous with it.
Source: http://barry.warsaw.us/software/laws.html
segunda-feira, julho 24, 2006
YouOS - A Web Operating System
YouOS is an experiment in a new kind of computing platform.
https://www.youos.com
https://www.youos.com
sábado, julho 22, 2006
The Top 20 Most Critical Internet Security Vulnerabilities
Top Vulnerabilities in Windows Systems
W1. Windows Services
W2. Internet Explorer
W3. Windows Libraries
W4. Microsoft Office and Outlook Express
W5. Windows Configuration Weaknesses
Top Vulnerabilities in Cross-Platform Applications
C1. Backup Software
C2. Anti-virus Software
C3. PHP-based Applications
C4. Database Software
C5. File Sharing Applications
C6. DNS Software
C7. Media Players
C8. Instant Messaging Applications
C9. Mozilla and Firefox Browsers
C10. Other Cross-platform Applications
Top Vulnerabilities in UNIX Systems
U1. UNIX Configuration Weaknesses
U2. Mac OS X
Top Vulnerabilities in Networking Products
N1. Cisco IOS and non-IOS Products
N2. Juniper, CheckPoint and Symantec Products
N3. Cisco Devices Configuration Weaknesses
Source: http://www.sans.org/top20
W1. Windows Services
W2. Internet Explorer
W3. Windows Libraries
W4. Microsoft Office and Outlook Express
W5. Windows Configuration Weaknesses
Top Vulnerabilities in Cross-Platform Applications
C1. Backup Software
C2. Anti-virus Software
C3. PHP-based Applications
C4. Database Software
C5. File Sharing Applications
C6. DNS Software
C7. Media Players
C8. Instant Messaging Applications
C9. Mozilla and Firefox Browsers
C10. Other Cross-platform Applications
Top Vulnerabilities in UNIX Systems
U1. UNIX Configuration Weaknesses
U2. Mac OS X
Top Vulnerabilities in Networking Products
N1. Cisco IOS and non-IOS Products
N2. Juniper, CheckPoint and Symantec Products
N3. Cisco Devices Configuration Weaknesses
Source: http://www.sans.org/top20
terça-feira, julho 18, 2006
Server monitoring
To make all sorts of graphs:
apt-get install munin munin-node
Example: http://munin.ping.uio.no
To compute more statistics:
* anteater
* isoqlog
* mailgraph
Monitor system logs: logcheck:
* sends you mail with abnormal log lines
* It's important to customize what is normal and you do it with regular expressions
Source: http://www.enricozini.org/blog/eng/seventh-day-in-addis.html
apt-get install munin munin-node
Example: http://munin.ping.uio.no
To compute more statistics:
* anteater
* isoqlog
* mailgraph
Monitor system logs: logcheck:
* sends you mail with abnormal log lines
* It's important to customize what is normal and you do it with regular expressions
Source: http://www.enricozini.org/blog/eng/seventh-day-in-addis.html
Games for Linux
http://forums.gentoo.org/viewtopic-t-429035-postdays-0-postorder-asc-highlight-monsterz-start-0.html
segunda-feira, julho 17, 2006
Phoronix Linux Compatible Hardware
Phoronix LCH is designed to be a community-driven indexing system for computer hardware under GNU/Linux. This system allows you to post GNU/Linux information on hardware as well as sharing your own personal experiences when it comes to GNU/Linux compatibility. You are also able to browse and search the database for other hardware as well. This is designed to make it much more effortless when deciding what GNU/Linux compatible hardware to go with during your next upgrade. Phoronix LCH is not distribution specific, and allows comments from all versions of GNU/Linux. Phoronix LCH is to spread what works and what doesn't when it comes to hardware under Linux.
http://www.phoronix.com/lch
http://www.phoronix.com/lch
sábado, julho 15, 2006
Dell laptop explodes at Japanese conference
Fully Open Source NTFS Support Under Linux
The Linux NTFS project has released a beta version of its fully open source userspace (using FUSE) 3G-Linux NTFS support driver. According to the developer, this driver beats hands down other NTFS support solutions performance-wise (including commercial Paragon NTFS driver and also Captive NTFS, which is using windows ntfs.sys driver under WINE).
http://www.linux-ntfs.org
http://www.linux-ntfs.org
terça-feira, julho 04, 2006
The Ten Most Critical Wireless and Mobile Security Vulnerabilities
1. Default WiFi routers: By default, wireless routers are shipped in an un-secured state.
2. Rogue Access Points: set up an authorized access point, without informing the network administrator.
3. Wireless Zero Configuration: When a computer connects to an access point, it generally stores the details of that connection locally. The next time the computer is turned on, the wireless network card immediately looks for the connection and re-establishes the connection. Since the SSID value is sent as plain text, anyone with a sniffer can see it. Programs like Karma automate this process.
4. Bluetooth exploits: BlueSnarfing, BlueBugging, BlueJacking, BlueTooth DoS attacks.
5. WEP Weaknesses: passwords can easily be cracked using Airsnort.
6. Clear Text Encryption Passwords: Some of the most popular mobile encryption programs even store the password in plain text in the registry.
7. Malicious Code: "Airborne" mobile viruses.
8. Autorun: Windows Mobile devices contain a little-known autorun feature that can provide an attacker with a quick and easy method of infection. When a media card is inserted into the PDA, Windows Mobile will copy over the autorun.exe (if it exists), create a copy in the /Windows directory, and execute it. A user can prevent this by creating a read-only dummy executable called autorun.exe and put it in the /Windows folder.
9. Multiple VoIP attacks: VoIP is mostly sent in an unencrypted format. As a result, anyone can see the connection information and capture/record the conversation. Programs like VoMiT and Cain & Abel can easily capture and record conversations. Other programs like sipbomber can kick a user offline. In addition, SiVus (a VoIP scanner) can quickly locate VoIP enabled systems.
10. Lost and stolen devices: All mobile databases should be encrypted. A good, written security policy and user education are also important. Mobile devices should all have a login copyright banner, along with return information.
Fonte: Help Net Security ( http://www.net-security.org/article.php?id=927&p=1 )
2. Rogue Access Points: set up an authorized access point, without informing the network administrator.
3. Wireless Zero Configuration: When a computer connects to an access point, it generally stores the details of that connection locally. The next time the computer is turned on, the wireless network card immediately looks for the connection and re-establishes the connection. Since the SSID value is sent as plain text, anyone with a sniffer can see it. Programs like Karma automate this process.
4. Bluetooth exploits: BlueSnarfing, BlueBugging, BlueJacking, BlueTooth DoS attacks.
5. WEP Weaknesses: passwords can easily be cracked using Airsnort.
6. Clear Text Encryption Passwords: Some of the most popular mobile encryption programs even store the password in plain text in the registry.
7. Malicious Code: "Airborne" mobile viruses.
8. Autorun: Windows Mobile devices contain a little-known autorun feature that can provide an attacker with a quick and easy method of infection. When a media card is inserted into the PDA, Windows Mobile will copy over the autorun.exe (if it exists), create a copy in the /Windows directory, and execute it. A user can prevent this by creating a read-only dummy executable called autorun.exe and put it in the /Windows folder.
9. Multiple VoIP attacks: VoIP is mostly sent in an unencrypted format. As a result, anyone can see the connection information and capture/record the conversation. Programs like VoMiT and Cain & Abel can easily capture and record conversations. Other programs like sipbomber can kick a user offline. In addition, SiVus (a VoIP scanner) can quickly locate VoIP enabled systems.
10. Lost and stolen devices: All mobile databases should be encrypted. A good, written security policy and user education are also important. Mobile devices should all have a login copyright banner, along with return information.
Fonte: Help Net Security ( http://www.net-security.org/article.php?id=927&p=1 )
segunda-feira, julho 03, 2006
Partimage
Partition Image is a Linux/UNIX utility which saves partitions in many formats (see below) to an image file. The image file can be compressed in the GZIP/BZIP2 formats to save disk space, and split into multiple files to be copied on removable floppies (ZIP for example), ... Partitions can be saved across the network since version 0.6.0.
http://www.partimage.org
http://www.partimage.org
segunda-feira, junho 26, 2006
nUbuntu

The main goal of nUbuntu is to create a distribution which is derived from the Ubuntu distribution, and add packages related to security testing, and remove unneeded packages, such as Gnome, Openoffice.org, and Evolution. nUbuntu is the result of an idea two people had to create a new distribution for the learning experience. Many people ask, "What makes it better than X?", or "Why should I use this over Y". Our answer to this question is, we do not think about whether people are using it or not. We are more concerned about the learning process. If you want to try something with a clean interface, fast, and an excellent range of programs please don't hesitate to download nUbuntu.
http://www.nubuntu.org
domingo, junho 25, 2006
Top 100 Network Security Tools
After the tremendously successful 2000 and 2003 security tools surveys, Insecure.Org is delighted to release this 2006 survey. Fyodor asked users from the nmap-hackers mailing list to share their favorite tools, and 3,243 people responded. This allowed me to expand the list to 100 tools, and even subdivide them into categories. Anyone in the security field would be well advised to go over the list and investigate tools they are unfamiliar with.
http://sectools.org
http://sectools.org
domingo, junho 18, 2006
Sistemas Operacionais na Copa 2006
FIFA World Cup - FreeBSD
Yahoo! - FreeBSD
Phillips - FreeBSD
Toshiba - Solaris 9 / FreeBSD
McDonalds - Solaris 8 / FreeBSD
Coca-Cola Company - Linux / IBM Appliances
Adidas - Linux / Windows 2003
Budweiser - Windows 2000
Avaya - Solaris 8 / Windows 200 / FreeBSD
Continental - Linux / IBM
Deutsche Telekom - Solaris 8 / FreeBSD
Fly Emirates - Windows 2003
Fuji Film - Solaris 8
Gillette - Windows 2000
Mastercard - Solaris 8 / FreeBSD / Windows 2000
Fonte: FUG-BR ( http://www.fug.com.br/content/view/64/54 )
Yahoo! - FreeBSD
Phillips - FreeBSD
Toshiba - Solaris 9 / FreeBSD
McDonalds - Solaris 8 / FreeBSD
Coca-Cola Company - Linux / IBM Appliances
Adidas - Linux / Windows 2003
Budweiser - Windows 2000
Avaya - Solaris 8 / Windows 200 / FreeBSD
Continental - Linux / IBM
Deutsche Telekom - Solaris 8 / FreeBSD
Fly Emirates - Windows 2003
Fuji Film - Solaris 8
Gillette - Windows 2000
Mastercard - Solaris 8 / FreeBSD / Windows 2000
Fonte: FUG-BR ( http://www.fug.com.br/content/view/64/54 )
quinta-feira, junho 15, 2006
Red Hat Knowledgebase
Red Hat Knowledgebase is a library of tips, troubleshooting advice, and current information updated daily by Red Hat technicians.
http://kbase.redhat.com
http://kbase.redhat.com
quarta-feira, junho 07, 2006
Ubuntu Weekly Newsletter
Ubuntu Weekly Newsletter - Reporting all of this weeks Ubuntu, Kubuntu, Edubuntu and Xubuntu action.
https://wiki.ubuntu.com/UbuntuWeeklyNewsletter
https://wiki.ubuntu.com/UbuntuWeeklyNewsletter
terça-feira, junho 06, 2006
DSPAM
DSPAM is one of the web's premiere anti-spam solutions, written by Jonathan Zdziarski. These pages are devoted to explaining how to install and use DSPAM.
http://dspamwiki.expass.de
http://dspamwiki.expass.de
domingo, junho 04, 2006
Automatix for Dapper and Breezy
http://www.ubuntuforums.org/showthread.php?t=177646
Items for specifically Breezy or Dapper will have a BR-Breezy, DP-Dapper or BD for both.
Capabilities:
1) Installs multimedia codecs - BD
2) Installs all Firefox plugins (java, flash, etc) (except Adobe reader and mplayer) - BD
3) Installs RAR, ACE and UNRAR archive support - BD
4) Installs skype - BD
5) Installs Acrobat reader 7 and firefox plugin for the same. - BD
6) Installs Gnomebaker (CD/DVD burning s/w for GNOME) - BD
7) Installs gftp (FTP client for GNOME with ssh capability) - BD
8) Installs Frostwire (GPL clone of Limewire) - BD
9) Installs multimedia editors (Audacity (audio), Kino (video), EasyTag (ID3)) - BD
10) Installs DVD (dvdrip) ripper - BD
11) Installs Mplayer and mplayerplug for Firefox - BD
12) Installs totem-xine, Realplayer, VLC and Beep Media Player (with docklet) - BD
13) Installs Opera Browser - BD
14) Installs Debian Menu (shows all installed applications) (this kills and restarts your gnome-panel without warning u but its a completely harmless operation!) - BD
15) Installs Bittornado and Azureus (Bittorrent clients) - BD
16) Installs Avidemux (Video editing tool) (New version 2.1.0) - BD
17) Enables Numlock on (turns numlock on Gnome startup) - BD
18) Installs Programming Tools (Anjuta (C/C++ IDE), Bluefish (HTML editor), Screem (Web Development Env.) and NVU (HTML editor)) - BD
19) Install GnomePPP (Graphical Dial up connection tool) - BD
20) Installs MS true type fonts - BD
21) Configures ctrl-alt-del to start gnome-system-monitor (aka windows) - BD
22) Installs Streamripper and Streamtuner - BD
23) Installs NON-FREE audio and dvd codecs - BD
24) Installs ndisgtk (WiFi configurator Graphical user interface) - BD
25) Upgrades Open Office to 2.0 (final version), installs openoffice clipart and installs OO2 thumbnailer. - BR
26) Adds 3 nautilus scripts (open any file with gedit as root; open a nautilus window as root in any folder; open gnome search tool in any folder (Right click in a nautilus window and look under "scripts") - BD
27) Installs SUN'S JAVA JRE version 1.5 - BD
28) Installs SUN'S JAVA JDK version 1.5 - BD
29) Installs wine (u need to run winecfg manually after installation) - BD
30) Enables ejection of CD when CDROM drive button is pressed. - BD
31) Installs AMSN 0.95 (MSN client with webcam support) - BD
32) Installs Mercury Messenger (Java based MSN client with webcam support) - BR
33) Installs BUM (Boot-up Manager) - BD
34) Installs DCPP (Linux DC++ client) - BD
35) Installs sbackup (Backup and restoration solution) - BD
36) Installs the latest version of Rhythmbox - DP
37*) Installs firestarter (GNOME firewall frontend) and adds firestarter to GNOME startup - BR
38*) installs gdesklets (GNOME eyecandy) and adds gdesklets to GNOME startup - BD
39*) Gamepads (Makes USB gamepads work) - BR
40*) Turns DMA ON on Intel and AMD machines (needs a restart) - BR
41*) NVIDIA cards (Detects Nvidia cards and installs drivers) (Needs a restart) - BD
42*) Adds midi capability to your Ubuntu box (test by playing a midi file with timidity or pmidi from terminal) - BR
43*) Installs Firefox 1.5.0.3 and its plugins(themes and extensions are not retained.bookmarks need to be copied from backup folder) - BR
44*) Installs Mozilla-Thunderbird 1.5 (US-only version) (no support for non-US-english language packs and enigmail) - BD
45*) Fixes Gnome sound related issues (ALSA and ESD config) (needs a restart) (ONLY FOR GNOME! NOT TO BE USED ON KDE/XFCE) - BR
Items for specifically Breezy or Dapper will have a BR-Breezy, DP-Dapper or BD for both.
Capabilities:
1) Installs multimedia codecs - BD
2) Installs all Firefox plugins (java, flash, etc) (except Adobe reader and mplayer) - BD
3) Installs RAR, ACE and UNRAR archive support - BD
4) Installs skype - BD
5) Installs Acrobat reader 7 and firefox plugin for the same. - BD
6) Installs Gnomebaker (CD/DVD burning s/w for GNOME) - BD
7) Installs gftp (FTP client for GNOME with ssh capability) - BD
8) Installs Frostwire (GPL clone of Limewire) - BD
9) Installs multimedia editors (Audacity (audio), Kino (video), EasyTag (ID3)) - BD
10) Installs DVD (dvdrip) ripper - BD
11) Installs Mplayer and mplayerplug for Firefox - BD
12) Installs totem-xine, Realplayer, VLC and Beep Media Player (with docklet) - BD
13) Installs Opera Browser - BD
14) Installs Debian Menu (shows all installed applications) (this kills and restarts your gnome-panel without warning u but its a completely harmless operation!) - BD
15) Installs Bittornado and Azureus (Bittorrent clients) - BD
16) Installs Avidemux (Video editing tool) (New version 2.1.0) - BD
17) Enables Numlock on (turns numlock on Gnome startup) - BD
18) Installs Programming Tools (Anjuta (C/C++ IDE), Bluefish (HTML editor), Screem (Web Development Env.) and NVU (HTML editor)) - BD
19) Install GnomePPP (Graphical Dial up connection tool) - BD
20) Installs MS true type fonts - BD
21) Configures ctrl-alt-del to start gnome-system-monitor (aka windows) - BD
22) Installs Streamripper and Streamtuner - BD
23) Installs NON-FREE audio and dvd codecs - BD
24) Installs ndisgtk (WiFi configurator Graphical user interface) - BD
25) Upgrades Open Office to 2.0 (final version), installs openoffice clipart and installs OO2 thumbnailer. - BR
26) Adds 3 nautilus scripts (open any file with gedit as root; open a nautilus window as root in any folder; open gnome search tool in any folder (Right click in a nautilus window and look under "scripts") - BD
27) Installs SUN'S JAVA JRE version 1.5 - BD
28) Installs SUN'S JAVA JDK version 1.5 - BD
29) Installs wine (u need to run winecfg manually after installation) - BD
30) Enables ejection of CD when CDROM drive button is pressed. - BD
31) Installs AMSN 0.95 (MSN client with webcam support) - BD
32) Installs Mercury Messenger (Java based MSN client with webcam support) - BR
33) Installs BUM (Boot-up Manager) - BD
34) Installs DCPP (Linux DC++ client) - BD
35) Installs sbackup (Backup and restoration solution) - BD
36) Installs the latest version of Rhythmbox - DP
37*) Installs firestarter (GNOME firewall frontend) and adds firestarter to GNOME startup - BR
38*) installs gdesklets (GNOME eyecandy) and adds gdesklets to GNOME startup - BD
39*) Gamepads (Makes USB gamepads work) - BR
40*) Turns DMA ON on Intel and AMD machines (needs a restart) - BR
41*) NVIDIA cards (Detects Nvidia cards and installs drivers) (Needs a restart) - BD
42*) Adds midi capability to your Ubuntu box (test by playing a midi file with timidity or pmidi from terminal) - BR
43*) Installs Firefox 1.5.0.3 and its plugins(themes and extensions are not retained.bookmarks need to be copied from backup folder) - BR
44*) Installs Mozilla-Thunderbird 1.5 (US-only version) (no support for non-US-english language packs and enigmail) - BD
45*) Fixes Gnome sound related issues (ALSA and ESD config) (needs a restart) (ONLY FOR GNOME! NOT TO BE USED ON KDE/XFCE) - BR
domingo, maio 28, 2006
Linux wireless LAN support
This is an attempt to create a, more or less complete listing of wireless devices with information about the chipset they are based on and whether or not they are supported in Linux. The basis of this list came from this list.
This list isn't complete, so if you have any information about a wireless card, its chipset and whether or not it is supported, please help to support.
This list doesn't specify anything about how much of your card is supported. So a card that only works without encryption is listed the same as one that also has support for WEP/WPA. For the specifics about how much of your card is supported, please refer to the driver page listed for your card.
http://linux-wless.passys.nl
This list isn't complete, so if you have any information about a wireless card, its chipset and whether or not it is supported, please help to support.
This list doesn't specify anything about how much of your card is supported. So a card that only works without encryption is listed the same as one that also has support for WEP/WPA. For the specifics about how much of your card is supported, please refer to the driver page listed for your card.
http://linux-wless.passys.nl
quinta-feira, maio 18, 2006
sexta-feira, maio 12, 2006
sábado, maio 06, 2006
GTER-21 e GTS-7 em Porto Alegre
GTER 21ª Reunião, Porto Alegre - 26 e 27 de Junho de 2006:
http://gter.nic.br/reunioes/gter-21
GTS-7, a se realizar em Porto Alegre. 26 e 27 de junho de 2006:
http://gts.nic.br/reunioes/gts-7
http://gter.nic.br/reunioes/gter-21
GTS-7, a se realizar em Porto Alegre. 26 e 27 de junho de 2006:
http://gts.nic.br/reunioes/gts-7
quinta-feira, abril 27, 2006
Linux Performance Tuning
When a distribution is packaged and delivered to clients, it is designed to be fully compatible with most of the computers available in the market. This is a very heterogeneous set of hardware (hard disks, video cards, network cards, etc.). So distribution vendors like Red Hat, SuSe, Mandriva and the rest of them choose some conservative configuration options to assure a successful installation.
http://www.linuxforums.org/desktop/linux_performance_tuning.html
http://www.linuxforums.org/desktop/linux_performance_tuning.html
sábado, abril 22, 2006
quarta-feira, abril 12, 2006
segunda-feira, abril 10, 2006
Theodore Ts'o

One of the core kernel developers for the Linux operating system. Implemented and maintained the serial driver, POSIX job control, POSIX signal handling, and the ext2 filesystem utilities. Chair of the Technical Board for Linux International. Developed a device driver for the Rocketport intelligent serial board on contract for Comtrol, Inc. Maintainer of the TSX-11.MIT.EDU ftp site (first ftp in U.S.A. to house Linux).
quinta-feira, abril 06, 2006
Squid Result Codes
TCP_HIT
A valid copy of the requested object was in the cache.
TCP_MISS
The requested object was not in the cache.
TCP_REFRESH_HIT
The requested object was cached but STALE. The IMS query for the object resulted in "304 not modified".
TCP_REF_FAIL_HIT
The requested object was cached but STALE. The IMS query failed and the stale object was delivered.
TCP_REFRESH_MISS
The requested object was cached but STALE. The IMS query returned the new content.
TCP_CLIENT_REFRESH_MISS
The client issued a "no-cache" pragma, or some analogous cache control command along with the request. Thus, the cache has to refetch the object.
TCP_IMS_HIT
The client issued an IMS request for an object which was in the cache and fresh.
TCP_SWAPFAIL_MISS
The object was believed to be in the cache, but could not be accessed.
TCP_NEGATIVE_HIT
Request for a negatively cached object, e.g. "404 not found", for which the cache believes to know that it is inaccessible. Also refer to the explainations for negative_ttl in your squid.conf file.
TCP_MEM_HIT
A valid copy of the requested object was in the cache and it was in memory, thus avoiding disk accesses.
TCP_DENIED
Access was denied for this request.
TCP_OFFLINE_HIT
The requested object was retrieved from the cache during offline mode. The offline mode never validates any object, see offline_mode in squid.conf file.
UDP_HIT
A valid copy of the requested object was in the cache.
UDP_MISS
The requested object is not in this cache.
UDP_DENIED
Access was denied for this request.
UDP_INVALID
An invalid request was received.
UDP_MISS_NOFETCH
During "-Y" startup, or during frequent failures, a cache in hit only mode will return either UDP_HIT or this code. Neighbours will thus only fetch hits.
NONE
Seen with errors and cachemgr requests.
The following codes are no longer available in Squid-2:
ERR_*
Errors are now contained in the status code.
TCP_CLIENT_REFRESH
See: TCP_CLIENT_REFRESH_MISS.
TCP_SWAPFAIL
See: TCP_SWAPFAIL_MISS.
TCP_IMS_MISS
Deleted, TCP_IMS_HIT used instead.
UDP_HIT_OBJ
Hit objects are no longer available.
UDP_RELOADING
See: UDP_MISS_NOFETCH.
A valid copy of the requested object was in the cache.
TCP_MISS
The requested object was not in the cache.
TCP_REFRESH_HIT
The requested object was cached but STALE. The IMS query for the object resulted in "304 not modified".
TCP_REF_FAIL_HIT
The requested object was cached but STALE. The IMS query failed and the stale object was delivered.
TCP_REFRESH_MISS
The requested object was cached but STALE. The IMS query returned the new content.
TCP_CLIENT_REFRESH_MISS
The client issued a "no-cache" pragma, or some analogous cache control command along with the request. Thus, the cache has to refetch the object.
TCP_IMS_HIT
The client issued an IMS request for an object which was in the cache and fresh.
TCP_SWAPFAIL_MISS
The object was believed to be in the cache, but could not be accessed.
TCP_NEGATIVE_HIT
Request for a negatively cached object, e.g. "404 not found", for which the cache believes to know that it is inaccessible. Also refer to the explainations for negative_ttl in your squid.conf file.
TCP_MEM_HIT
A valid copy of the requested object was in the cache and it was in memory, thus avoiding disk accesses.
TCP_DENIED
Access was denied for this request.
TCP_OFFLINE_HIT
The requested object was retrieved from the cache during offline mode. The offline mode never validates any object, see offline_mode in squid.conf file.
UDP_HIT
A valid copy of the requested object was in the cache.
UDP_MISS
The requested object is not in this cache.
UDP_DENIED
Access was denied for this request.
UDP_INVALID
An invalid request was received.
UDP_MISS_NOFETCH
During "-Y" startup, or during frequent failures, a cache in hit only mode will return either UDP_HIT or this code. Neighbours will thus only fetch hits.
NONE
Seen with errors and cachemgr requests.
The following codes are no longer available in Squid-2:
ERR_*
Errors are now contained in the status code.
TCP_CLIENT_REFRESH
See: TCP_CLIENT_REFRESH_MISS.
TCP_SWAPFAIL
See: TCP_SWAPFAIL_MISS.
TCP_IMS_MISS
Deleted, TCP_IMS_HIT used instead.
UDP_HIT_OBJ
Hit objects are no longer available.
UDP_RELOADING
See: UDP_MISS_NOFETCH.
Http Status Codes
000 Used mostly with UDP traffic.
100 Continue
101 Switching Protocols
*102 Processing
200 OK
201 Created
202 Accepted
203 Non-Authoritative Information
204 No Content
205 Reset Content
206 Partial Content
*207 Multi Status
300 Multiple Choices
301 Moved Permanently
302 Moved Temporarily
303 See Other
304 Not Modified
305 Use Proxy
[307 Temporary Redirect]
400 Bad Request
401 Unauthorized
402 Payment Required
403 Forbidden
404 Not Found
405 Method Not Allowed
406 Not Acceptable
407 Proxy Authentication Required
408 Request Timeout
409 Conflict
410 Gone
411 Length Required
412 Precondition Failed
413 Request Entity Too Large
414 Request URI Too Large
415 Unsupported Media Type
[416 Request Range Not Satisfiable]
[417 Expectation Failed]
*424 Locked
*424 Failed Dependency
*433 Unprocessable Entity
500 Internal Server Error
501 Not Implemented
502 Bad Gateway
503 Service Unavailable
504 Gateway Timeout
505 HTTP Version Not Supported
*507 Insufficient Storage
600 Squid header parsing error
100 Continue
101 Switching Protocols
*102 Processing
200 OK
201 Created
202 Accepted
203 Non-Authoritative Information
204 No Content
205 Reset Content
206 Partial Content
*207 Multi Status
300 Multiple Choices
301 Moved Permanently
302 Moved Temporarily
303 See Other
304 Not Modified
305 Use Proxy
[307 Temporary Redirect]
400 Bad Request
401 Unauthorized
402 Payment Required
403 Forbidden
404 Not Found
405 Method Not Allowed
406 Not Acceptable
407 Proxy Authentication Required
408 Request Timeout
409 Conflict
410 Gone
411 Length Required
412 Precondition Failed
413 Request Entity Too Large
414 Request URI Too Large
415 Unsupported Media Type
[416 Request Range Not Satisfiable]
[417 Expectation Failed]
*424 Locked
*424 Failed Dependency
*433 Unprocessable Entity
500 Internal Server Error
501 Not Implemented
502 Bad Gateway
503 Service Unavailable
504 Gateway Timeout
505 HTTP Version Not Supported
*507 Insufficient Storage
600 Squid header parsing error
segunda-feira, abril 03, 2006
quinta-feira, março 30, 2006
domingo, março 26, 2006
Tabela comparativa dos chips da ATI e nVidia
ATI:
http://www.clubedohardware.com.br/artigos/520
nVidia:
http://www.clubedohardware.com.br/artigos/519
http://www.clubedohardware.com.br/artigos/520
nVidia:
http://www.clubedohardware.com.br/artigos/519
quinta-feira, março 16, 2006
Desvendando o /proc
http://www-128.ibm.com/developerworks/linux/library/l-proc.html?ca=dgr-lnxw02ProcFile
http://www-128.ibm.com/developerworks/linux/library/l-adfly.html
http://www.comptechdoc.org/os/linux/howlinuxworks/linux_hlproc.html
http://www.samag.com/documents/s=8920/sam0311a/0311a.htm
http://www-128.ibm.com/developerworks/linux/library/l-adfly.html
http://www.comptechdoc.org/os/linux/howlinuxworks/linux_hlproc.html
http://www.samag.com/documents/s=8920/sam0311a/0311a.htm
quinta-feira, março 02, 2006
The table of equivalents / replacements / analogs of Windows software in Linux
One of the biggest difficulties in migrating from Windows to Linux is the lack of knowledge about comparable software. Newbies usually search for Linux analogs of Windows software, and advanced Linux-users cannot answer their questions since they often don't know too much about Windows :). This list of Linux equivalents / replacements / analogs of Windows software is based on our own experience and on the information obtained from the visitors of this page (thanks!).
This table is not static since new application names can be added to both left and the right sides. Also, the right column for a particular class of applications may not be filled immediately. In future, we plan to migrate this table to the PHP/MySQL engine, so visitors could add the program themselves, vote for analogs, add comments, etc.
http://www.linuxrsp.ru/win-lin-soft/table-eng.html
This table is not static since new application names can be added to both left and the right sides. Also, the right column for a particular class of applications may not be filled immediately. In future, we plan to migrate this table to the PHP/MySQL engine, so visitors could add the program themselves, vote for analogs, add comments, etc.
http://www.linuxrsp.ru/win-lin-soft/table-eng.html
terça-feira, fevereiro 28, 2006
sábado, fevereiro 25, 2006
quinta-feira, fevereiro 23, 2006
GTK no Ubuntu usando KDE
Para mudar os temas GTK no Ubuntu:
# apt-get install gtk-theme-switch gtk-engines-geramik
$ gtk-theme-switch2
# apt-get install gtk-theme-switch gtk-engines-geramik
$ gtk-theme-switch2
terça-feira, fevereiro 14, 2006
Os pinguins também jogam!
Um tour virtual pelos melhores jogos para Linux
http://linuxval.free.fr/games
http://linuxval.free.fr/games
quarta-feira, fevereiro 08, 2006
How to set up a mail server on a GNU / Linux system

Step by step guide to install Postfix
Ubuntu + Postfix + Courier IMAP + MySQL + Amavisd-new + SpamAssassin + ClamAV + SASL + TLS + SquirrelMail + Postgrey
http://flurdy.com/docs/postfix
quarta-feira, fevereiro 01, 2006
Pink e Cerebro
Page e Brin, fundadores do Google, estão no Brasil:

http://info.abril.com.br/aberto/infonews/012006/30012006-10.shl

http://info.abril.com.br/aberto/infonews/012006/30012006-10.shl
segunda-feira, janeiro 30, 2006
Wikitravel
Wikitravel é um projeto que visa criar um guia mundial de viagens gratuito, completo, atualizado e disponível para todos.
http://wikitravel.org/pt
http://wikitravel.org/pt
terça-feira, janeiro 10, 2006
sexta-feira, janeiro 06, 2006
Cyber Security Bulletin SB2005
http://www.us-cert.gov/cas/bulletins/SB2005.html
http://it.slashdot.org/article.pl?sid=06/01/06/1358225
http://it.slashdot.org/article.pl?sid=06/01/06/1358225
quarta-feira, janeiro 04, 2006
Assinar:
Postagens (Atom)